|
|
|
NETWORK CONCEPTS
BASIC NETWORK CONCEPTS
The basic reasons why computers are networked are
Take for example a typical office scenario where a number of users in a small business require access to common information. As long as all user computers are connected via a network, they can share their files, exchange mail, schedule meetings, send faxes and print documents all from any point of the network.
It would not be necessary for users to transfer files via electronic mail or floppy disk, rather, each user could access all the information they require, thus leading to less wasted time and hence greater productivity.
Imagine the benefits of a user being able to directly fax the Word document they are working on, rather than print it out, then feed it into the fax machine, dial the number etc.
Small networks are often called Local Area Networks [LAN]. A LAN is a network allowing easy access to other computers or peripherals. The typical characteristics of a LAN are,
BASIC NETWORK COMPONENTS
New cards are software configurable, using a software program to configure the resources used by the card. Other cards are PNP [plug and Play], which automatically configure their resources when installed in the computer, simplifying installation. With an operating system like Windows 95, auto-detection of new hardware makes network connections simple and quick.
On power-up, the computer detects the new network card, assigns the correct resources to it, and then installs the networking software required for connection to the network. All the user need do is assign the network details like computer name.
For Ethernet or
10BaseT cards, each card is identified by a twelve digit hexadecimal number. This number uniquely identifies the computer. These network card numbers are used in the Medium Access [MAC] Layer to identify the destination for the data. When talking to another computer, the data you send to that computer is prefixed with the number of the card you are sending the data to.This allows intermediate devices in the network to decide in which direction the data should go, in order to transport the data to its correct destination.
A typical adapter card looks like,
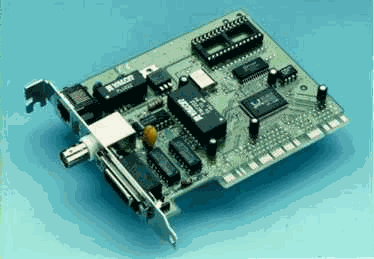
A PCMCIA adapter card, suitable for connecting to a portable laptop computer to a network, looks like,

Peripheral cards associated with EISA and MCA are normally self configuring.
The major problem arises with cards for the ISA bus (found in the majority of AT type computers and clones). This is because the cards are configured by the user (using either jumpers or a software program).
Users make mistakes, and often configure cards so that they conflict with other cards already present in this system. This causes intermittent or immediate non-operation of the computer system.
For instance, a networking card that is allocated the same resources as a serial communications program may function perfectly, except when the user is logged into the network and then tries to use the serial port, at which time the machine will crash.
Resources Used By Peripheral Cards
We have already mentioned that resources used by ISA peripheral cards must not be shared (two cards cannot use the same). So what are the resources used by peripheral cards? Essentially, there are FOUR resources which are user configurable for peripheral cards. Some cards may only use one (a port location(s)), others may require all four.
The FOUR resources are
This space is also sometimes used by a remote boot Eprom, which is used for diskless workstations which download the operating system from the server at boot time.
So How Do Peripheral Cards Work?
Peripheral cards require a software driver to function. This software driver provides the interface between the card and the operating system, making the services provided by the card available to the user.
The software driver is normally configured to match the resource settings of the card. This is done by a configuration utility, and stored either in the executable file, or a separate file (like .ini or .cfg).
It is obviously important for the configuration settings in the software driver to match those configured on the peripheral card.
The resources used by the card are either set by jumpers (or slide switches). New cards can also be configured using a software program, rather than by manually setting jumpers on the card. Where cards are software configurable, the cards retain their configuration when the power is turned off.
The software driver provides the follow functions
The basic operation looks something like,
The major problem is assigning values of these resources which are already being used by either the system or another peripheral card. It is therefore handy to know what the resources are which are used by common peripheral devices. The following tables identify these.
 Common I/O Port Addresses
Common I/O Port Addresses
|
Port Address |
Peripheral |
|
200-207h |
Game I/O Adaptor |
|
210-217h |
XT Expansion Unit |
|
220h |
SoundBlaster |
|
278-27Fh |
LPT2 |
|
2E8-2EFh |
COM4 |
|
2F8-2FFh |
COM2 |
|
300-30Fh |
Color Video Adaptor |
|
320-32F |
XT Hard Disk |
|
330h |
SoundBlaster MIDI |
|
378-37Fh |
LPT1 |
|
3A0-3A9h |
IBM Synchronous Adaptor |
|
3B0-3BFh |
Monochrome Video |
|
3E8-3EFh |
COM3 |
|
3F0-3F7h |
Floppy Disk |
|
3F8-3FFh |
COM1 |
Common Interrupts
|
IRQ Line |
Peripheral |
|
2 |
EGA/VGA |
|
3 |
COM2 |
|
4 |
COM1 |
|
5 |
LPT2, Bus mouse, Network |
|
6 |
Floppy Disk |
|
7 |
LPT1 |
|
13 |
Co-Processor |
|
14 |
AT Disk Controller |
Common Memory Addresses
|
Address |
Peripheral |
|
A0000-BFFFFh |
EGA/VGA |
|
B0000-B7FFFh |
Monochrome |
|
B8000-BFFFFh |
CGA |
|
C8000-CFFFFh |
XT Disk |
|
F4000-FFFFFh |
AT ROM BIOS |
|
F8000-FFFFFh |
PC/XT ROM BIOS |
Common DMA Lines
|
DMA Line |
Peripheral |
|
0 |
Memory Circuitry |
|
1 |
Spare |
|
2 |
Floppy Drive |
Installing A Peripheral Card
This section discusses basic techniques for installing peripheral cards. By following standardized procedures, this will help to minimize damage to the system or peripheral card, and reduce the possibility of incorrect installation.
Summary of Installing Network Cards in Servers and Workstations
Brief Guide to BUILDING WIRING
A building wiring system covers a number of different elements
Horizontal Wiring
The horizontal wiring extends from the wall outlet to the system center (telecommunications closet). It includes the
Some general features of the horizontal wiring scheme are
Backbone Wiring The backbone wiring system interconnects telecommunication closets, equipment rooms and entrance facilities (i.e., the outside world). Some general features are
EIA/TIA-568 WIRING STANDARD
The latest version is 568B, which contains some enhancements to the original standard.
The standard specifies
SIX subsystem components of the cable system,All horizontal cabling is implemented using a star topology, and must not exceed 90 meters from the TC to the wall outlet. A minimum of TWO outlets are required per work area, one of which must be wired with four-pair 100-ohm UTP cable.
The color coding of the UTP cable is,
The standard also specifies the use of an eight-pin modular RJ-45 jack for wall outlets using
Unshielded Twisted Pair (UTP).Categories of UTP Cabling
The EIA/TIA standard specifies FIVE categories of
EIA/TIA-568A Connector Specifications
This is gradually being phased out in favour of EIA/TIA-568B
|
Label |
Color Code |
Pin Number |
|
T3 |
White/Green |
1 |
|
R3 |
Green/White |
2 |
|
T2 |
White/Orange |
3 |
|
R1 |
Blue/White |
4 |
|
T1 |
White/Blue |
5 |
|
R2 |
Orange/White |
6 |
|
T4 |
White/Brown |
7 |
|
R4 |
Brown/White |
8 |
EIA/TIA-568B and AT&T258A Connector Specifications
Recommended by the IEEE for 100Base-TX and T4 operation
|
Label |
Color Code |
Pin Number |
|
T2 |
White/Orange |
1 |
|
R2 |
Orange/White |
2 |
|
T3 |
White/Green |
3 |
|
R1 |
Blue/White |
4 |
|
T1 |
White/Blue |
5 |
|
R3 |
Green/White |
6 |
|
T4 |
White/Brown |
7 |
|
R4 |
Brown/White |
8 |
IEEE 10Base-T Connector Specifications
|
Label |
Color Code |
Pin Number |
|
T2 |
White/Orange |
1 |
|
R2 |
Orange/White |
2 |
|
T3 |
White/Green |
3 |
|
R1 |
4 |
|
|
T1 |
5 |
|
|
R3 |
Green/White |
6 |
|
T4 |
7 |
|
|
R4 |
8 |
EIA/TIA-568 UTP Wiring Standard Specifications
100Base-T Wiring Standard Specifications
Fast Ethernet for Category 5 UTP. This standard is based on CDDI (
100Base-FX Wiring Standard Specifications
Fast Ethernet over Fiber Optic Cable
100Base-T4 Wiring Standard Specifications
Fast Ethernet for Category 3 UTP Cable
Cabling
Shielded twisted pair uses a special braided wire which surrounds all the other wires, which helps to reduce unwanted interference.
The features of twisted pair cable are,
Unshielded Twisted Pair cable used in Category 5 looks like

Category 5 cable uses 8 wires. The various jack connectors used in the wiring closet look like,

The patch cord which connects the workstation to the wall jack looks like,

Distance limitations exist when cabling. For category 5 cabling at 100Mbps, the limitations effectively limit a workstation to wall outlet of 3 meters, and wall outlet to wiring closet of 90 meters.
All workstations are wired back to a central wiring closet, where they are then patched accordingly. Within an organization, the IT department either performs this work or sub-contracts it to a third party.
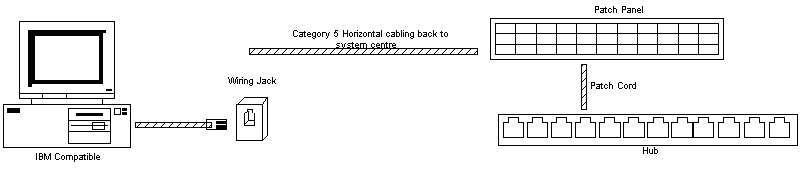
In 10BaseT, each PC is wired back to a central hub using its own cable. There are limits imposed on the length of drop cable from the PC network card to the wall outlet, the length of the horizontal wiring, and from the wall outlet to the wiring closet.
Patch Cables
Patch cables come in two varieties, straight through or reversed. One application of patch cables is for patching between modular patch panels in system centers. These are the straight through variety. Another application is to connect workstation equipment to the wall jack, and these could be either straight through or reversed depending upon the manufacturer. Reversed cables are normally used for voice systems.
 How to determine the type of patch cable
How to determine the type of patch cable
Align the ends of the cable side by side so that the contacts are facing you, then compare the colors from left to right.
If the colors are in the same order on both plugs, the cable is straight through. If the colors appear in the reverse order, the cable is reversed.
Coaxial Cable
The general features of coaxial cable are,
 Thin coaxial cable [RG-58AU rated at 50 ohms], as used in Ethernet LAN's, looks like
Thin coaxial cable [RG-58AU rated at 50 ohms], as used in Ethernet LAN's, looks like
The connectors used in thin-net Ethernet LAN's are T connectors (used to join cables together and attach to workstations) and terminators (one at each end of the cable). The T-connectors and terminators look like

Fiber Optic
The features of fiber-optic cable systems are,
 Fiber optic is often used to overcome distance limitations. It can be used to join two hubs together, which normally could not be connected due to distance limitations. In this instance, a UTP to Fiber transceiver [often referred to as a FOT] is necessary. Fiber optic cable looks like
Fiber optic is often used to overcome distance limitations. It can be used to join two hubs together, which normally could not be connected due to distance limitations. In this instance, a UTP to Fiber transceiver [often referred to as a FOT] is necessary. Fiber optic cable looks like
In addition, fiber optic patch panels are used to interconnect fiber cables. These patch panels look like

OSI Model
When we think of how to send data from one computer to another, there are many different things involved. There are network adapters, voltages and signals on the cable, how the data is packaged, error control in case something goes wrong, and many other concerns. By dividing these into separate layers, it makes the task of writing software to perform this much easier.
In the Open Systems Interconnect model, which allows dissimilar computers to transfer data between themselves, there are SEVEN distinct layers.
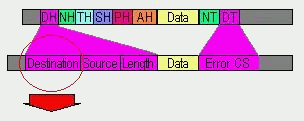
The Data-Link Layer also provides error-free delivery of data between the two computers by using the physical layer. It does this by packaging the data from the Network Layer into a frame which includes error detection information. At the receiving computer, the Data-Link Layer reads the incoming frame, and generates its own error detection information based on the received frames data. After receiving all of the frame, it then compares its error detection value with that of the incoming frames, and if they match, the frame has been received correctly.
A frame looks like,
![]()
For Ethernet 802.3, the Physical Layer can be represented as
Sending Data Via the OSI Model
Each layer acts as though it is communicating with its corresponding layer on the other end.
In reality, data is passed from one layer down to the next lower layer at the sending computer, till it's finally transmitted onto the network cable by the Physical Layer. As the data it passed down to a lower layer, it is encapsulated into a larger unit (in effect, each layer adds its own layer information to that which it receives from a higher layer). At the receiving end, the message is passed upwards to the desired layer, and as it passes upwards through each layer, the encapsulation information is stripped off .
NETWORK SEGMENTS
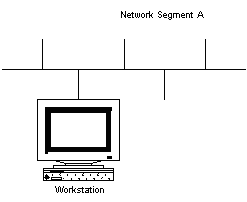
Large networks are made by combining several individual network segments together, using appropriate devices like routers and/or bridges.
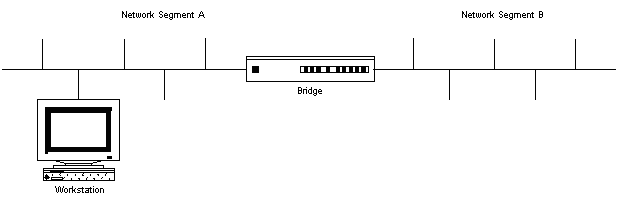
In the above diagram, a bridge is used to allow traffic from one network segment to the other. Each network segment is considered unique and has its own limits of distance and the number of connections possible.
When network segments are combined into a single large network, paths exist between the individual network segments. These paths are called routes, and devices like routers and bridges keep tables which define how to get to a particular computer on the network. When a packet arrives, the router/bridge will look at the destination address of the packet, and determine which network segment the packet is to be transmitted on in order to get to its destination.
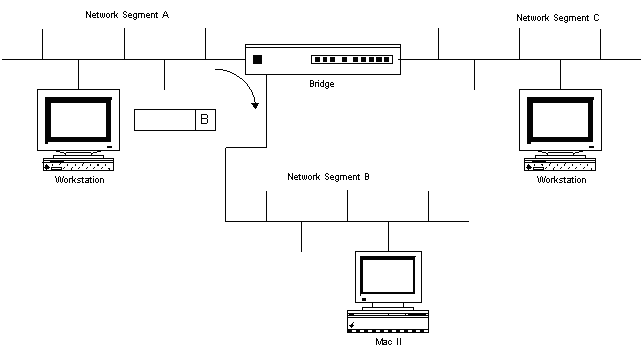
In the above diagram, a packet arrives whose destination is segment B. The bridge forwards this incoming packet from segment A to the B segment.
SPANNING TREE ALGORITHM
Sometimes, a loop would be created which caused the wrong packets to be sent on incorrect segments. These packets could loop around the network, being forwarded on, eventually arriving back, only to be forwarded on, etc. This quickly floods the network. The spanning tree algorithm is a software algorithm which defines how switches and bridges can communicate and avoid network loops.
Packets are exchanged between bridges/switches, and they establish a single path for reaching any particular network segment. This is a continuous process, so that if a bridge/switch fails, the remaining devices can reconfigure the routing tables to allow each segment to be reached.
To be effective, ensure that the bridges/switches in use in your network support this protocol.
REPEATERS
Repeaters also allow isolation of segments in the event of failures or fault conditions. Disconnecting one side of a repeater effectively isolates the associated segments from the network.
Using repeaters simply allows you to extend your network distance limitations. It does not give you any more bandwidth or allow you to transmit data faster.
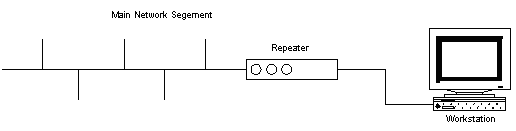
It should be noted that in the above diagram, the network number assigned to the main network segment and the network number assigned to the other side of the repeater are the same. In addition, the traffic generated on one segment is propagated onto the other segment. This causes a rise in the total amount of traffic, so if the network segments are already heavily loaded, it's not a good idea to use a repeater.
A repeater works at the
Physical Layer by simply repeating all data from one segment to another.
Summary of Repeater features
During initialization, the bridge learns about the network and the routes. Packets are passed onto other network segments based on the MAC layer. Each time the bridge is presented with a frame, the source address is stored. The bridge builds up a table which identifies the segment to which the device is located on. This internal table is then used to determine which segment incoming frames should be forwarded to. The size of this table is important, especially if the network has a large number of workstations/servers.
The advantages of bridges are
The disadvantages of bridges are
Transparent bridges
(also known as spanning tree, IEEE 802.1 D) make all routing decisions. The bridge is said to be transparent (invisible) to the workstations. The bridge will automatically initialize itself and configure its own routing information after it has been enabled.Bridges are ideally used in environments where there a number of well defined workgroups, each operating more or less independent of each other, with occasional access to servers outside of their localized workgroup or network segment. Bridges do not offer performance improvements when used in diverse or scattered workgroups, where the majority of access occurs outside of the local segment.
The diagram below shows two separate network segments connected via a bridge. Note that each segment must have a unique network address number in order for the bridge to be able to forward packets from one segment to the other.

Ideally, if workstations on network segment A needed access to a server, the best place to locate that server is on the same segment as the workstations, as this minimizes traffic on the other segment, and avoids the delay incurred by the bridge.
A bridge works at the
MAC Layer by looking at the destination address and forwarding the frame to the appropriate segment upon which the destination computer resides.
Summary of Bridge features
ROUTERS
Routers were devised in order to separate networks logically. For instance, a
TCP/IP router can segment the network based on groups of TCP/IP addresses. Filtering at this level (on TCP/IP addresses, also known as level 3 switching) will take longer than that of a bridge or switch which only looks at the MAC layer.Most routers can also perform bridging functions. A major feature of routers, because they can filter packets at a protocol level, is to act as a firewall. This is essentially a barrier, which prevents unwanted packets either entering or leaving designated areas of the network.
Typically, an organization which connects to the Internet will install a router as the main gateway link between their network and the outside world. By configuring the router with access lists (which define what protocols and what hosts have access) this enforces security by restricted (or allowing) access to either internal or external hosts.
For example, an internal WWW server can be allowed IP access from external networks, but other company servers which contain sensitive data can be protected, so that external hosts outside the company are prevented access (you could even deny internal workstations access if required).
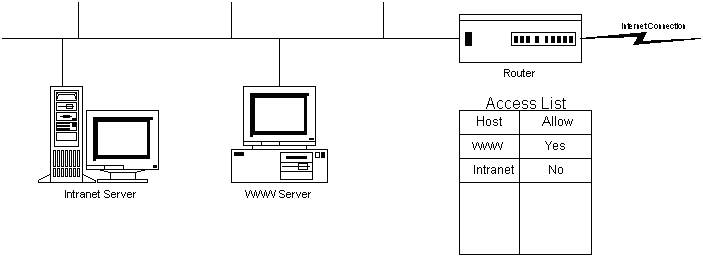
A router works at the
Network Layer or higher, by looking at information embedded within the data field, like a TCP/IP address, then forwards the frame to the appropriate segment upon which the destination computer resides.Summary of Router features
HUBS
Nowadays, with the advent of 10BaseT, hub concentrators are being very popular. These are very sophisticated and offer significant features which make them radically different from the older hubs which were available during the 1980's.
These 10BaseT hubs provide each client with exclusive access to the full bandwidth, unlike bus networks where the bandwidth is shared. Each workstation plugs into a separate port, which runs at 10Mbps and is for the exclusive use of that workstation, thus there is no contention to worry about like in Ethernet.
These 10BaseT hubs also include buffering of packets and filtering, so that unwanted packets (or packets which contain errors) are discarded. SNMP management is also a common feature.
In standard Ethernet, all stations are connected to the same network segment in bus configuration. Traffic on the bus is controlled using the
CSMA (Carrier Sense Multiple Access) protocol, and all stations share the available bandwidth. 10BaseT Hubs dedicate the entire bandwidth to each port (workstation). The workstations attach to the hub using UTP. The hub provides a number of ports, which are logically combined using a single backplane, which often runs at a much higher data rate than that of the ports.
10BaseT Hubs dedicate the entire bandwidth to each port (workstation). The workstations attach to the hub using UTP. The hub provides a number of ports, which are logically combined using a single backplane, which often runs at a much higher data rate than that of the ports.
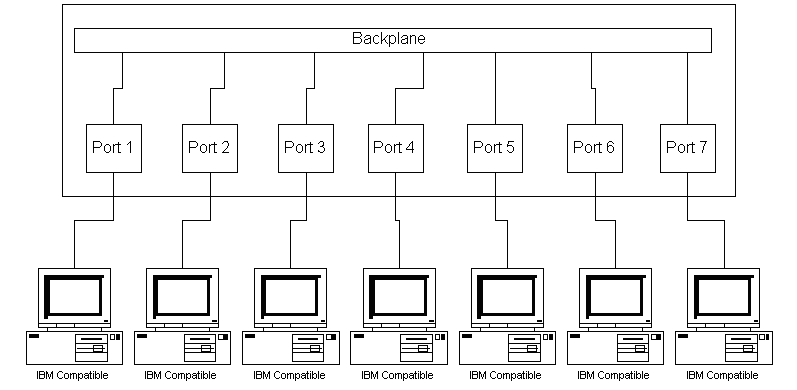
Ports can also be buffered, to allow packets to be held in case the hub or port is busy. And, because each workstation has it's own port, it does not contend with other workstations for access, having the entire bandwidth available for it's exclusive use.
The ports on a hub all appear as one Ethernet segment. In addition, hubs can be stacked or cascaded (using master/slave configurations) together, to add more ports per segment. As hubs do not count as repeaters, this is a better option for adding more workstations than the use of a repeater.
Hub options also include an SNMP (Simple Network Management Protocol) agent. This allows the use of network management software to remotely administer and configure the hub. Detailed statistics related to port usage and bandwidth are often available, allowing informed decisions to be made concerning the state of the network.
In summary, the advantages for these newer 10BaseT hubs are,
ETHERNET SWITCHES
When a packet arrives, the header is checked to determine which segment the packet is destined for, and then its forwarded to that segment. If the packet is destined for the same segment that it arrives on, the packet is dropped and not retransmitted. This prevents the packet being "broadcasted" onto unnecessary segments, reducing the traffic.
Nodes which inter-communicate frequently should be placed on the same segment. Switches work at the MAC layer level.

Switches divide the network into smaller collision domains [a collison domain is a group of workstations that contend for the same bandwidth]. Each segment into the switch has its own collision domain (where the bandwidth is competed for by workstations in that segment). As packets arrive at the switch, it looks at the MAC address in the header, and decides which segment to forward the packet to. Higher protocols like IPX and TCP/IP are buried deep inside the packet, so are invisible to the switch. Once the destination segment has been determined, the packet is forwarded without delay.
Each segment attached to the switch is considered to be a separate collision domain. However, the segments are still part of the same broadcast domain [a broadcast domain is a group of workstations which share the same network subnet, in TCP/IP this is defined by the subnet mask]. Broadcast packets which originate on any segment will be forwarded to all other segments (unlike a router). On some switches, it is possible to disable this broadcast traffic.
Some vendors implement a broadcast throttle feature, whereby a limit is placed on the number of broadcasts forwarded by the switch over a certain time period. Once a threshold level has been reached, no additional broadcasts are forwarded till the time period has expired and a new time period begins.
Cut-Through Switches
Cut through switches use either a cross-bar or cell-backplane architecture.
Store-Forward Switches
Back Pressure Switches
Switches often employ buffering of packets. This is done so when packets arrive for a busy port, the packet is temporarily stored till the port becomes free. When the buffer becomes fill, packets become lost.
Back pressure switches overcome this problem by sending the overflow packets back to the workstation. This effectively slows the workstation transmission rate, and hence slows the arrival of new packets at the port.
Ethernet Switching: Advantges
Virtual Networking
Any traffic generated by these workstations can be sent to any other workstation in that domain. Workstations outside that domain are unable to see any packets (including broadcasts) that belong to the secure domain. Obviously, this has enormous implications for developing secure networks. Multiple virtual workgroups can exist, like email and www server. Users can belong to more than one virtual domain, thereby administration is centralized and security is maintained. The use of switch technology makes this possible.